TL;DR
GoFileRoom made changes to their encryption by using TLS1.2. In order for GFR add-on to work in Windows Server, you must modify 2 registry entries for .NET enforcing strong encryption. For GFR website to operate, you need to ensure TLS1.2 is enabled as well.
Here’s the GoFileRoom technical notes on enabling this via Registry: http://cs.thomsonreuters.com/ua/gfr/digita_uk_en/kb/recommended-registry-changes-for-tls-1-2.htm?mybanner=1
How I got here…
Let me preface this with the fact that GoFileRoom is not officially supported on Server 2016, so my troubleshooting process was skewed because I was thinking there was an installation problem or some other incompatibility issue.
The GFR Windows add-on recently stopped working as reported by users on a terminal server. The error being thrown was right at the logon prompt of the GFR Add-on with the following message:
The service you are trying to reach is unavailable. Please try again later.
Digging around the system, I managed to find a logfile that GFR saves to, it is located in %APPDATA%\GoFileRoom\GFRControlPanel\logs
The log file didn’t give me a single hint:
[GoFileRoom.GFRUser]:[Login] Web Exception: The request was aborted: Could not create SSL/TLS secure channel.
When in doubt… procmon!
This didn’t directly answer any of my questions as to why… so, when in doubt, procmon! I went and grabbed ProcMon from SysInternals and ran it during a GFR session so I could figure out if there was some incompatibility.
ProcMon didn’t give me much of anything. I saw it was attempting an HTTPS connection to member.gofileroom.com, but nothing abnormal in terms of compatibility problems or something.
I went back to the GFR logfile message and did a quick Google for The request was aborted: Could not create SSL/TLS secure channel.
The first result was a StackOverflow post and it was a great post with two points of interest to me:
- Mentions of TLS 1.2 via HTTPWebRequest method
- SChannel logging
This got the wheels in my head turning — There was one specific comment that said to look for a TLS 1.2 support issue and another comment about enabling logging for SChannel.
I knew IE was configured with TLS properly as that was one of the first things I checked (per GFR installation guidelines). But there’s something different here. It seems the GFR add-on is calling an HTTPWebRequest method and that is where this error message is being generated from!
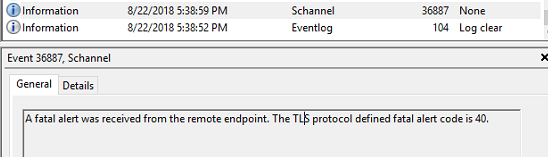
Further into the thread of comments and proposed solutions, there was a note about enabling SChannel – totally forgot about this as I wasn’t thinking it was a TLS negotiation issue! I enabled SChannel logging at level 7 (all messages) and reproduced the error. Fired up event viewer and saw what I needed:
A fatal alert was received from the remote endpoint. The TLS protocol defined fatal alert code is 40.
No idea what code 40 is, so off to MSDN.
An MSDN article tells me it is a handshake_failure. Awesome, now I have a better search term to try for Google: gofileroom tls
Guess what? First result is a GoFileRoom KB article. See the TL;DR for the link.
#net-framework, #gfr, #gofileroom, #tls