Microsoft Internet Explorer Vulnerability: CVE-2014-1776
 I have been inundated with questions about the latest vulnerability relating to Microsoft Internet Explorer and thought I would put together a brief post to use for reference. Microsoft has issued a Security Advisory detailing this a bit more in-depth if you’re interested.
I have been inundated with questions about the latest vulnerability relating to Microsoft Internet Explorer and thought I would put together a brief post to use for reference. Microsoft has issued a Security Advisory detailing this a bit more in-depth if you’re interested.
Am I Affected?
If you use Internet Explorer on Windows XP, Vista, 7, or 8/8.1/8.1U1 – yes, you are affected. If you use Internet Explorer on Microsoft Windows Server platforms (2003, 2003R2, 2008, 2008R2, 2012, 2012R2) you may not be affected if Enhanced Security Configuration is still enabled as this mitigates the vulnerability. ESC is enabled by default on the Microsoft Windows Server platforms but server administrators have been known to disable this not only for Administrators but for Users which would make the systems vulnerable. Affected version of Internet Explorer:
- Internet Explorer 6
- Internet Explorer 7
- Internet Explorer 8
- Internet Explorer 9
- Internet Explorer 10
- Internet Explorer 11
Note Windows RT is affected, but not really. Windows RT does not allow installation of software outside the Windows Store, so although it is technically affected, it’s technically also not affected.
How can I Protect Myself?
Get EMET 4.0+
I cannot strongly enough recommend downloading and installing Microsoft’s EMET tool. This tool mitigates this vulnerability, as well as many more and is available free from Microsoft. EMET is the Ehanced Mitigation Experience Toolkit designed to help protect applications from exposure to certain vulnerabilities by adding another layer of protection.
Windows 8 and Internet Explorer 10: If you have Internet Explorer 10 and are on Windows 8, KB2790907 must be installed to use EMET.
Windows XP users take note: You will not be receiving a patch when Microsoft publishes a fix, however, you can still download and use EMET to mitigate this as well as use a few of the workarounds mentioned below.
Is there a Workaround?
Yes, there are quite a few options actually to help mitigate this vulnerability. The following method is what I prefer. Other methods include:
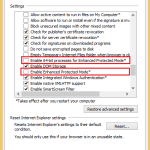
- Enable Enhanced Protection Mode
- Set Internet Zone security to High to make running ActiveX objects Prompt before running.
- This would be extremely annoying to most users since it would be prompting almost all the time when visiting any modern website.
- Change ACL on VGX.dll
- This method can cause headaches down the road during Windows Updates if you do not remember to change the ACL back.
- Unregister VGX.DLL
- This is my preferred method and will get re-registered upon later Windows Updates installations.
Unregister VGX.DLL
I think this is ultimately the best workaround. Why? This is targeting the source of the problem. Unregister the vgx.dll file. This is the source of the issue and by disabling this file, you will no longer have support for VML. Don’t know what VML is? You probably don’t need it. Maybe double-check with your IT folks before doing this. Open a command prompt, or paste the following (including the quotes) into the Start > Run box.
"%SystemRoot%System32\regsvr32.exe" -u "%CommonProgramFiles%\Microsoft Shared\VGXvgx.dll"
Example output: [caption id=“attachment_311” align=“alignnone” width=“673”]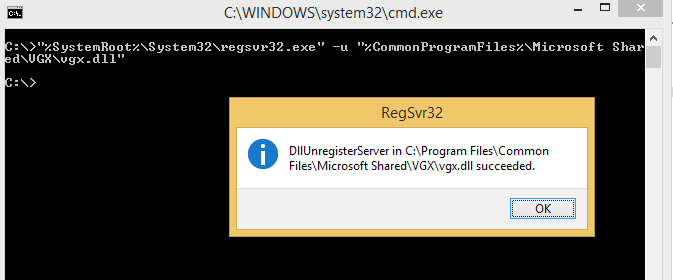 Unregister VPX.DLL[/caption]
Unregister VPX.DLL[/caption]
Revisions
2014-04-30 - fixed typos (vpx>vgx) thanks @jduck 2014-04-29 - fixed command typo, added ‘-u’ as it was omitted